Chapter 7 - GNSS Denial
A receiver can not provide position, navigation or time because the GNSS signals are not available to the receiver due to interference, spoofing, signal blockage or constellation failure is said to be suffering from “GNSS Denial”. The following sections describe the causes of GNSS denial and the methods used to mitigate them.
Interference
By the time GNSS signals have travelled from the satellites to the receiver, the signals are at a very low power level. This low power level makes the signals susceptible to interference from other signals transmitted in the GNSS frequency range. If the interfering signal is sufficiently powerful, it becomes impossible for the receiver to detect the low power GNSS signal. An analogy is trying to have a conversation in a room with a stereo playing. If the stereo is playing very loud, it is impossible to hear the conversation over the music.
If the signal is from an unintentional source, such as faulty radio equipment, it is called interference. If the signal is intentionally transmitted in the GNSS frequency range, it is called jamming. GNSS receivers use several methods to protect against interference and jamming.
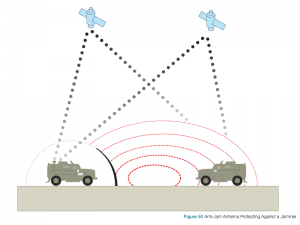
Anti-Jam Antennas
Anti-jam antenna systems, comprised of Controlled Reception Pattern Antennas (CRPA) and sophisticated electronics, use the multiple antenna elements to control the amount of signal received from a particular direction. When an anti-jam system senses interference from one direction, it turns down the antenna gain, similar to turning down the volume, for that direction. This reduces the amount of interference received so that legitimate GNSS signals can be received from other directions.
Figure 50 shows two vehicles in range of a GNSS jammer. The vehicle on the right has a standard antenna and the GNSS signals are overpowered by the jammer. The vehicle on the left has an anti-jam antenna that blocks the jamming signal so GNSS signals can be received.
If the interfering signal has a narrow bandwidth, GNSS receivers can protect against the interference by tracking multiple frequencies and multiple constellations. For example, if the interference is in the 1550 to 1600 MHz range, GPS L1 would be blocked. However, a receiver can still provide position, navigation and time if the receiver can track GPS L2 or L5, GLONASS L2 or Galileo E5. A description of the existing and upcoming GNSS signals is given in Chapter 3.
Multiple Navigation Sensors
For short term interference, additional navigation sensors, such as Inertial Measurement Units (IMUs), odometers or altimeters can help the receiver bridge brief periods of GNSS outage. A discussion of systems that use GNSS receivers and IMUs, called GNSS+Inertial Navigation Systems (INS) is presented in Chapter 6.
Spoofing
Unlike interference where GNSS is denied by overpowering the GNSS signal, spoofing tricks the receiver into reporting an incorrect location or time by introducing a false signal that is either created by a signal generator or is a rebroadcast of a real recorded GNSS signal. Also, unlike interference, spoofing is always an intentional attack.
To deny GNSS by spoofing, the attacker broadcasts a signal with the same structure and frequency as the GNSS signal. The spoofing signal controls its transmitted power level so the receiver will lock onto the spoofed signal rather than the real GNSS signal. In the spoofed signal, the message is changed so that the receiver will calculate an incorrect position or time.
The most effective way to protect against spoofing is to track an encrypted signal (such as the Y-code signal on GPS L1 and L2) that is broadcast by several of the GNSS constellations. Access to the encrypted signals is restricted and not available to all users, however there are mitigation methods that can be used with open signal receivers.
Spoofing GNSS signals is complicated and requires sophisticated equipment. It also generally needs information about the velocity of the target. The complexity of spoofing increases greatly if the attacker attempts to simultaneously spoof more than one GNSS frequency or constellation. So, a receiver that can track multiple frequencies and/or multiple constellations can be used to detect and overcome a possible spoofing attempt.
Also, other navigation sensors, such as GNSS+INS, can be used to detect and overcome a spoofing attempt as the signals from the IMU cannot be spoofed.
Signal Blockage
A GNSS receiver needs a clear line of sight to the satellites it is tracking. If the line of sight to a satellite is blocked by objects such as buildings, trees, bridges, etc., the receiver cannot receive signals from that satellite. In locations that have a lot of obstructions, such as the downtown area of a large city, the obstructions can block so many satellites that the receiver cannot calculate its position or time.
One solution to signal blockage is for the receiver to track more than one constellation. By tracking more than one constellation, there will be more satellites available and a better chance of finding enough satellites to determine a position and time. The use of multiple navigation sensors, such as IMUs, helps not only in bridging outages such as those due to signal blockage, but also in reacquisition of the GNSS signals after the outage.
Constellation Failure
Although it is extremely unlikely that an entire constellation will fail, receivers that can track more than one constellation provide protection from this unlikely scenario.
Closing Remarks
With the many technologies and applications depending on the GNSS to provide position, navigation and time, the topic of GNSS Denial is becoming increasingly important. If you want to learn more about this subject, we have provided a list of references at the end of the book.